Connecting the Dots

Have you ever wondered how the internet seamlessly bridges continents, allowing us to communicate and share information at the click of a button? The answer lies beneath the waves, where a remarkable network of undersea cables forms the backbone of our interconnected world.
The Submarine Cable Network: A Modern Engineering Marvel

Picture vast lengths of fiber-optic cables, delicately laid across the ocean floor, connecting one continent to another. This intricate web, known as the submarine cable network, is an engineering marvel that facilitates the majority of our international internet traffic.
So, the next time you send an email to a friend across the ocean or watch a video from a different continent, take a moment to marvel at the invisible infrastructure working beneath the waves. The undersea cable network is a testament to human ingenuity, connecting us in ways that were once unimaginable. It's a reminder that, in our digital age, the world truly is at our fingertips, thanks to the silent lifelines beneath the sea.
Network
A network is a collection of interconnected computers, devices, or nodes that communicate and share resources with each other.

These connections can be established through various means, such as wired (e.g., Ethernet cables) or wireless (e.g., Wi-Fi) technologies. The primary purpose of a network is to facilitate the exchange of information, data, or resources between the connected entities.
Different types of Networks

Local Area Network (LAN):
Connection: Computers are physically close, often within a building.
Medium: Uses Ethernet cables or Wi-Fi for connectivity.
Topology: Common topologies include star and bus configurations.
Example: Office setups for local communication and resource sharing.
Metropolitan Area Network (MAN):
Connection: Computers span a city or a large campus.
Medium: Utilizes high-capacity network infrastructure like fiber-optic cables.
Topology: Combination of LAN-like configurations linking multiple locations.
Example: University campuses or business branches within a city.
Wide Area Network (WAN):
Connection: Connects computers over a broad geographical area, often global.
Medium: Utilizes long-distance technologies such as leased lines and the Internet.
Topology: Diverse topologies; the internet is a global example.
Example: Multinational corporations connecting offices worldwide for global communication.
Topology
A topology refers to the physical or logical arrangement of the elements within a network. It defines how different nodes (devices or computers) are connected and how data is transmitted between them. Various topologies are used to design networks based on factors such as scalability, reliability, and ease of maintenance.

Types of topologies
Bus Topology:
All devices share a single communication line (bus).
Simple and cost-effective for small networks.
Performance may degrade as more devices are added.
Star Topology:
All devices are connected to a central hub or switch.
Easy to install and manage.
Failure of one device doesn't affect others, but the central hub is critical.
Ring Topology:
Each device is connected to exactly two other devices, forming a ring.
Data travels in one direction, simplifying data collision issues.
Failure of one device can disrupt the entire network.
Mesh Topology:
Devices are interconnected, creating multiple paths for data to travel.
Offers high reliability and redundancy.
Complex and expensive to implement.
Hybrid Topology:
Combination of two or more different topologies.
Provides a balance between the advantages and disadvantages of individual topologies.
Offers flexibility and scalability.
Tree Topology:
Combination of star and bus topologies.
Groups of star-configured networks connected to a main bus backbone.
Hierarchical structure.
Basics of Network
We will further dig a deep dive into Networking fundamentals that involve the basic principles that govern how computers communicate and share information. Here's a very brief overview:
Communication: Networking enables devices, like computers and smartphones, to share data with each other. This communication can be within a local environment or across the globe.
Protocols: Networking relies on protocols, which are rules and conventions that devices follow to communicate. Examples include TCP/IP, HTTP, and DNS.
IP Addresses: Every device on a network is assigned a unique identifier called an IP address. It's like a virtual address that helps devices find and communicate with each other.
Routing: Data travels through networks by following paths, known as routes. Routers manage the flow of data between different networks.
Switching: Within a network, switches manage the direct communication between devices. They forward data only to the specific device it's intended for.
Firewalls: Firewalls are security devices that control the flow of data in and out of a network. They help protect against unauthorized access and potential threats.
DNS (Domain Name System): DNS translates human-readable domain names (like www.example.com) into IP addresses, making it easier for users to access websites.
Ethernet: Ethernet is a common technology for wired local area networks (LANs). It defines how data is transmitted over cables between devices.
Wireless Networking: Wi-Fi technology enables devices to connect to networks without physical cables. It's widely used for local and internet connectivity.
Subnetting: Subnetting involves dividing a larger network into smaller, more manageable sub-networks. It aids in efficient IP address management.
These fundamentals form the basis for understanding how networks operate and how devices interact with each other to enable communication and information exchange.
Protocols
A protocol is a set of rules or guidelines that define how data is transmitted and received in a network. It serves as a common language that allows different devices and systems to communicate with each other effectively. Protocols ensure that communication is standardized, enabling interoperability between diverse components of a network. These rules govern various aspects of data transmission, including the format of data packets, error handling, and the sequence of actions performed during communication.

Here's a brief explanation of different types of protocols:
HTTP (Hypertext Transfer Protocol):
- What it does: HTTP is the foundation of data communication on the World Wide Web. It is a protocol used for transmitting hypertext, which includes links, text, and multimedia, between web browsers and servers. When you type a web address in your browser, it sends an HTTP request to the server to retrieve the web page.
TCP (Transmission Control Protocol):
- What it does: TCP is a connection-oriented protocol that ensures the reliable and ordered delivery of data between devices on a network. It establishes a connection, manages the flow of data, and provides error checking and correction. It's commonly used for applications that require accurate and complete data transmission, such as file transfers and web pages.
UDP (User Datagram Protocol):
- What it does: UDP is a connectionless protocol that provides faster but less reliable data transmission compared to TCP. It's used for applications where some data loss is acceptable, such as real-time streaming, online gaming, or VoIP (Voice over Internet Protocol). UDP is faster because it doesn't establish a connection before sending data and doesn't provide error checking.
DHCP (Dynamic Host Configuration Protocol):
- What it does: DHCP is a network protocol used to automatically assign IP addresses and other network configuration information to devices on a network. When a device joins a network, it can send a DHCP request to a DHCP server, which then provides the device with an IP address, subnet mask, default gateway, and other parameters needed for communication on the network. DHCP simplifies network configuration and management.
IP address
An IP (Internet Protocol) address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves two main purposes: host or network interface identification and location addressing.

IP addresses come in two versions:
IPv4 (32-bit): In the common IPv4 format, an IP address looks like a series of four numbers separated by periods, such as "192.168.0.1." Each of these numbers can range from 0 to 255, providing a total of over four billion unique combinations.
Example: 192.168.0.1
IPv6 (128-bit): IPv6 is the latest Internet Protocol, providing a much larger pool of unique addresses (128 bits) compared to IPv4. It addresses the exhaustion of IPv4 addresses, enhances security, and supports the ever-growing number of devices connected to the internet. IPv6 addresses are represented in a hexadecimal format.
Example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Ports
A port is a communication endpoint that identifies a specific process or service on a device in a network. It is a 16-bit unsigned integer, thus allowing for a total of 65,536 different ports. Ports are used to distinguish between different services or applications running on a single device, enabling multiple network services to operate concurrently on the same device.
In the context of DevOps, ports play a crucial role in facilitating communication between various components of a distributed system. DevOps is a set of practices that aims to automate and streamline the collaboration between development and operations teams throughout the software development lifecycle.

Here are key points about ports and their uses:
Port Number:
A port is identified by a numerical value known as the port number.
Port numbers range from 0 to 65535, with certain ranges reserved for specific purposes.
Types of Ports:
Well-Known Ports (0-1023): Reserved for common services like HTTP (port 80), HTTPS (port 443), FTP (port 21), etc.
Registered Ports (1024-49151): Assigned by the Internet Assigned Numbers Authority (IANA) for specific purposes.
Dynamic or Private Ports (49152-65535): Available for temporary use by applications.
Uses of Ports in DevOps:
Service Accessibility: Ports are used to make services accessible over a network. For example, a web server may use port 80 for HTTP requests.
Networking Protocols: Ports are associated with specific networking protocols. For instance, SSH (Secure Shell) typically uses port 22, while FTP (File Transfer Protocol) uses ports 20 and 21.
Container Orchestration: Platforms like Kubernetes use ports for managing and coordinating communication between different components of the cluster.
Firewall Configuration: DevOps engineers often configure firewalls to allow or restrict traffic based on specific ports. This is crucial for security and controlling access to services.
Load Balancing: Load balancers distribute incoming network traffic across multiple servers. Ports are used to direct traffic to specific services on each server.
APIs and Web Services: APIs and web services often expose specific ports for communication. For example, a RESTful API might use port 8080 for HTTP communication.
Routing
Routing is the process of directing data packets between different networks, ensuring they reach their intended destinations. This involves determining the most efficient path for data to travel through a network of interconnected devices, known as routers. Routers are like traffic directors, making decisions about the best routes for data to reach its destination.
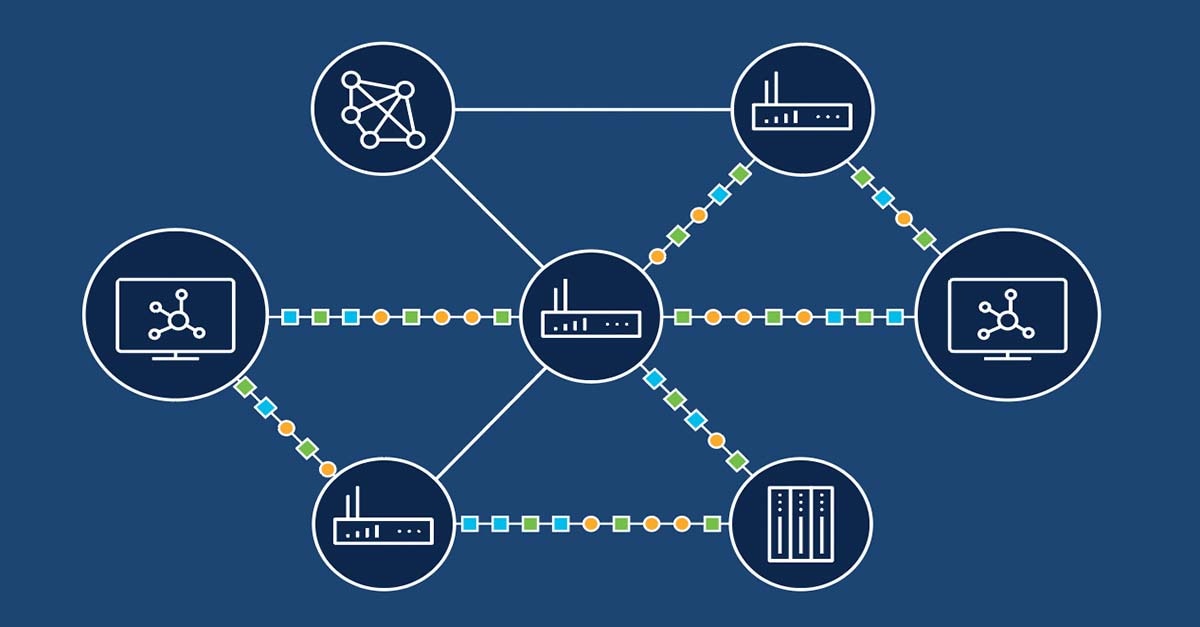
In a DevOps context, here are some key concepts related to routing in DevOps:
Microservices Communication: Applications are broken down into smaller, independent services & need to communicate with each other, thereby routing plays a crucial role in directing requests between microservices.
Load Balancing: Load balancing involves distributing incoming network traffic across multiple servers to ensure no single server is overwhelmed.
Container Orchestration: In containerized environments managed by orchestration tools like Kubernetes, routing is crucial for directing traffic to the appropriate containers.
Service Discovery: Service discovery involves locating and identifying services in a dynamic and scalable environment. Efficient routing ensures that requests are directed to the correct service instances.
Traffic Management in CI/CD Pipelines: DevOps involves the automation of Continuous Integration/Continuous Deployment (CI/CD) pipelines. Routing is essential for orchestrating the flow of data through various stages of the pipeline.
Firewalls
Firewalls play a critical role in ensuring the security and integrity of the infrastructure. It acts as a barrier between trusted internal networks and untrusted external networks, controlling incoming and outgoing traffic based on predefined security rules.

Some of the uses of Firewall:
Microservices Security: In a microservices architecture, various services communicate with each other. Firewalls help control and secure the communication channels between these microservices.
Cloud Security: Cloud-based firewalls are used to control traffic to and from virtual machines, applications, and other resources in the cloud environment.
Access Control: Firewalls help enforce access control policies by allowing or blocking specific types of traffic based on rules. This is crucial for limiting access to sensitive systems and resources.
Securing CI/CD Pipelines: (CI/CD) pipelines are central to DevOps practices. Firewalls are used to secure the flow of data within these pipelines, preventing unauthorized access and protecting sensitive information.
DNS (Domain Name System)
DNS, or the Domain Name System, is a crucial component of the internet that translates human-readable domain names into IP addresses. Computers and network devices communicate using IP addresses, which are numerical identifiers. However, humans find it easier to remember domain names (like www.example.com) than IP addresses.

DNS serves as a distributed database, essentially acting as the internet's phone book. When you type a domain name into a web browser, your computer queries DNS servers to obtain the corresponding IP address, allowing it to locate and connect to the desired web server.
In simpler terms, DNS is like the internet's address book, helping your computer find the correct destination when you type in a familiar domain name.
Subnetting
In a DevOps environment, where infrastructure is often distributed across various servers and devices, IP subnetting becomes crucial for efficient network management. DevOps teams use IP subnetting to logically divide large IP address spaces into smaller, more manageable subnets. This allows them to organize resources, control traffic flow, and implement security measures effectively.
For example, imagine a cloud environment where different applications and services run on separate subnets. IP subnetting helps ensure that communication between these components is well-organized and secure. DevOps engineers might allocate specific subnets for different purposes, such as application servers, databases, or testing environments.
Think of your neighborhood as a vast network, and each house has a unique address, like a device on the internet. Now, IP subnetting is like dividing the neighborhood into smaller blocks or streets. This helps keep things organized – maybe one street for families, another for businesses – making it easier to manage and control who can go where.
CIDR Range (Classless Inter-Domain Routing)
CIDR notation is an integral part of IP subnetting, providing a concise way to represent IP address ranges. In the context of DevOps, understanding CIDR ranges is crucial for tasks like defining security groups, configuring routing tables, and managing access control lists.
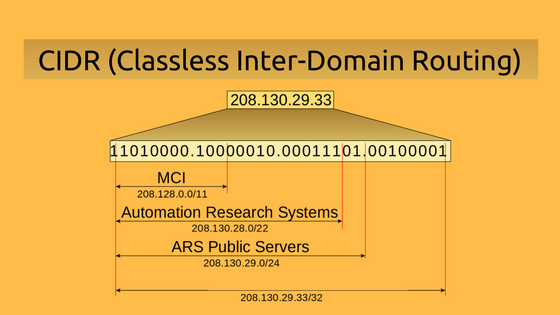
DevOps professionals often work with cloud services where CIDR ranges play a role in defining the scope of IP addresses that can communicate with each other. For instance, when setting up security groups in AWS, specifying CIDR ranges helps control which IP addresses are allowed to access specific resources.
Now, when we talk about CIDR range, imagine you want to give directions to your friend in the neighborhood. Instead of listing every house number, you can say, "Go to houses 1 to 100 on Main Street." In the digital world, CIDR range is a shorthand way of saying which groups of addresses belong together.
In DevOps, it's like setting rules for who can access which part of the digital city. If you say "192.168.1.0/24," it means a specific block of addresses, much like saying "Main Street from house 1 to 100." This helps in managing and securing the flow of digital traffic in the vast online neighborhood.
VPN (Virtual Private Network)
A VPN is a technology that establishes a secure, encrypted connection over the internet between different parts of a distributed infrastructure or between a user and a network. It enables secure communication, data transfer, and access to resources as if the connected devices were physically in the same location.

Uses of VPN in DevOps:
Secure Remote Access: DevOps teams often work remotely or need access to resources in different locations. A VPN provides a secure way for team members to connect to the corporate network or specific servers remotely.
Site-to-Site Connectivity: In a distributed infrastructure, various components or environments may be hosted in different physical locations or cloud providers. A VPN establishes secure connections between these sites, allowing seamless communication.
Data Encryption for CI/CD Pipelines: (CI/CD) pipelines involve the transfer of code and sensitive data. Using a VPN ensures that data transferred during the CI/CD process is encrypted and secure.
Access Control for Cloud Services: DevOps teams commonly use cloud services for scalability and flexibility. A VPN can be used to create a secure connection between on-premises infrastructure and cloud resources, controlling access.
OSI Model
The open systems interconnection (OSI) model is a conceptual model created by the International Organization for Standardization which enables diverse communication systems to communicate using standard protocols.

Sure, let's break down the OSI model, starting from the Application Layer, in simple terms:
Application Layer (Layer 7 - Software You Use):
- Imagine you're using an app on your phone or a program on your computer. The Application Layer is like that software. It's what you interact with directly—like your web browser, email client, or video chat application.
Presentation Layer (Layer 6 - Making Things Understandable):
- This layer is like a translator. Imagine you're sending a message in a secret code, and your friend needs to decode it. The Presentation Layer makes sure that the information from the Application Layer is in a format that both your device and the receiving device can understand.
Session Layer (Layer 5 - Setting Up and Ending Communication):
- Think of the Session Layer as the one responsible for starting and ending conversations. It sets up the connection between your device and the other device, like making a phone call, and makes sure the conversation runs smoothly.
Transport Layer (Layer 4 - Reliable Delivery):
- Now, your message needs a reliable way to travel. The Transport Layer is like a trustworthy delivery service. It breaks your message into smaller, manageable parts, sends them to the destination, and ensures they arrive in the correct order.
Network Layer (Layer 3 - Finding the Right Path):
- If your message needs to travel across different towns or cities, the Network Layer is like the guide directing it through the right path. It deals with addressing and routing, making sure your message reaches the correct destination.
Data Link Layer (Layer 2 - Local Delivery):
- This layer is like the local postman. It takes care of delivering your message within the same city or local area. It adds necessary details (like MAC addresses) to your message, ensuring it gets to the right device on the same network.
Physical Layer (Layer 1 - Actual Transmission):
- Now, your message is ready for the physical journey. The Physical Layer deals with the actual transmission of signals, whether it's through cables, Wi-Fi, or other means. It's like the roads or airways that your message uses to travel from one place to another.
So, in summary, the OSI model is like a set of organized steps to ensure that your digital messages, like texts, pictures, or videos, can be sent from one device to another in a way that both devices can understand. Each layer has its specific role, working together to make sure your communication happens smoothly and reliably.
TCP/IP Model
The TCP/IP (Transmission Control Protocol/Internet Protocol) model is a four-layer architecture that serves as the foundation for internet communication. It consists of the following layers:

Application Layer:
The top layer that interacts with end-user applications and provides network services directly to users.
Protocols at this layer support functions such as file transfers (FTP), email (SMTP), web browsing (HTTP), and domain name resolution (DNS).
Transport Layer:
Manages end-to-end communication and ensures reliable data transfer between applications on different devices.
Key protocols include Transmission Control Protocol (TCP) for connection-oriented communication and User Datagram Protocol (UDP) for connectionless communication.
Internet Layer:
Handles logical addressing, routing, and packet forwarding between different networks.
The primary protocol at this layer is Internet Protocol (IP), responsible for addressing and routing data packets across the global internet.
Link Layer (or Network Interface Layer):
Deals with the physical connection between devices and the local network.
Protocols at this layer include Ethernet, Wi-Fi (802.11), and others, ensuring the reliable transmission of data between devices within the same network.
In summary, the TCP/IP model starts with the Application Layer, where end-user applications interact with the network, and proceeds through the Transport Layer for end-to-end communication, the Internet Layer for logical addressing and routing, and finally, the Link Layer for physical network connections.
Conclusion
We have gone through the networking basics that reveal the language and architecture of our digital world. From diverse network types to the role of protocols, understanding these fundamentals is key.
Ports act as gatekeepers, routing directs data, and firewalls ensure security, VPNs secure remote access, CIDR define digital territories, and routing orchestrates data flow. OSI and TCP/IP models provide blueprints for comprehending communication layers.
As we navigate this digital landscape—from undersea cables to virtual highways—we appreciate the web connecting our modern world. The internet stands as a testament to innovation, ensuring the global village remains just a click away.
Hope you like my post. Don't forget to like, comment, and share.
